In today’s article, we are going to deploy Argo CD using Helm, complete with proper SSL and ingress configurations.
Prerequisites:
Before starting, ensure you have the following:
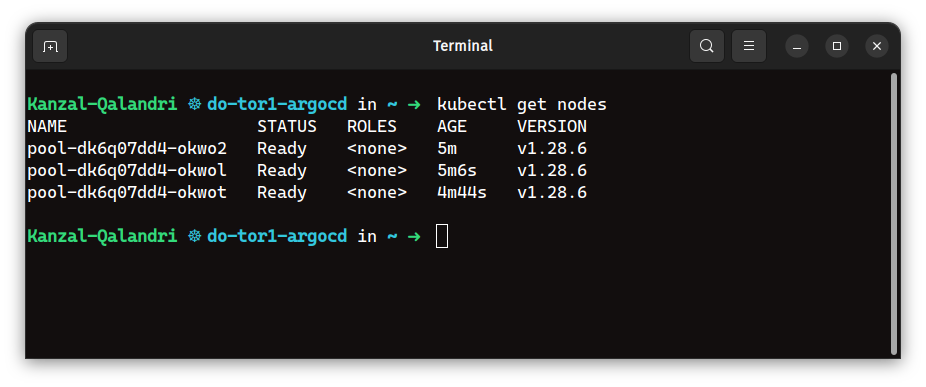
a) A Kubernetes Cluster (Obviously):
You need a Kubernetes cluster with proper access to it. I am using a managed Kubernetes cluster provided by DigitalOcean.
b) Helm Installed:
You need Helm installed on your machine to create resources on the Kubernetes cluster. Ensure the config file of the cluster is present inside ~/.kube/config. You can check if Helm is installed on your machine by running the command this command.
helm version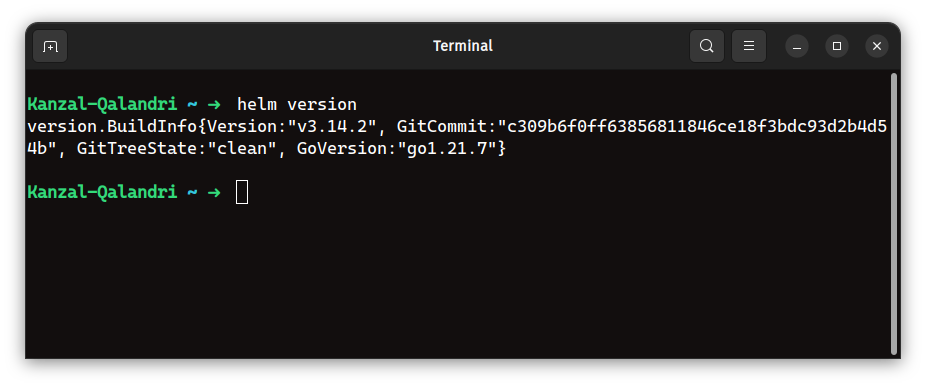
As you can see, I am using version v3.14.2 of Helm.
c) A Registered Domain or Subdomain:
You need a domain or subdomain to expose Argo CD on the web. I am using the subdomain argocd.kanzal.com. Additionally, you need to update the DNS records for your domain.
d) An SSL Certificate for Your Domain:
We need an SSL certificate to secure Argo CD. For this tutorial, I am using a free SSL certificate from Let’s Encrypt. I am generating the SSL certificate from sslforweb.com, but keep in mind that this is just for this test deployment.
Generally, in production, we use a wildcard certificate from GoDaddy or AWS. The process to generate the SSL certificate from sslforweb.com is very straightforward. You can check this article if you are facing some issues. Click Here
e) An Ingress Controller Installed in the Kubernetes Cluster:
We also need an ingress controller deployed in the cluster. This ingress controller deploys a load balancer where we will point our domain. In my setup, I am using the Nginx ingress controller from the DigitalOcean marketplace, deployed in my Kubernetes cluster. You can use one according to your setup.
1: Creating a TLS Secret:
Remember, we have generated an SSL certificate from sslforweb.com. I have downloaded certificate.crt and private.key.
Now, we need to create a TLS secret in the Kubernetes cluster. The name should be exactly “argocd-server-tls“.
The command to create a TLS secret with kubectl is:
kubectl create secret tls argocd-server-tls --cert=path/to/tls.cert --key=path/to/tls.keyThen, run the command below to check if the secret was created:
kubectl get secrets argocd-server-tls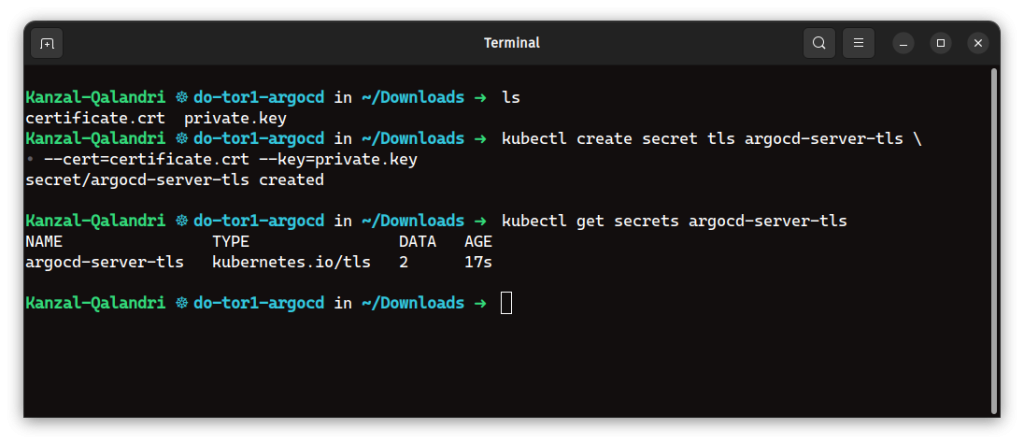
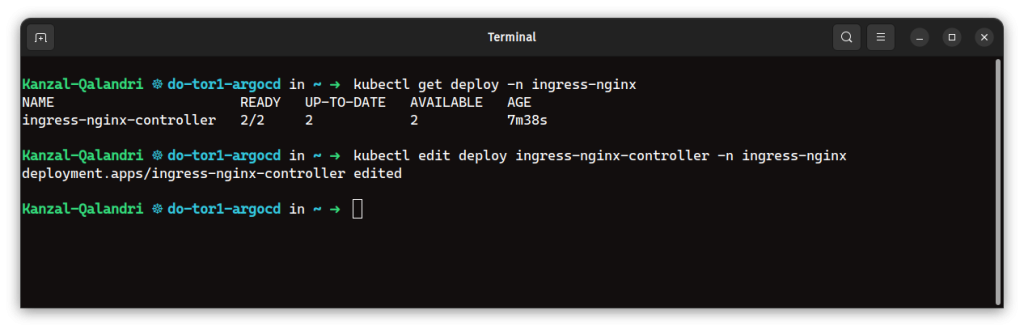
2: Updating the Ingress Controller:
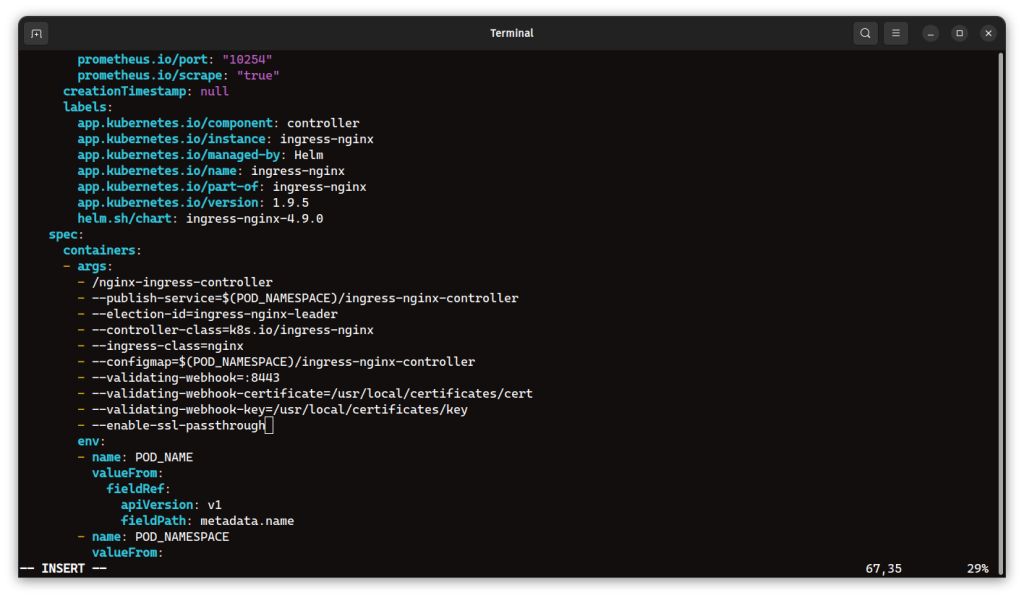
You need to update the arguments of the Ingress controller deployment by adding the – -enable-ssl-passthrough command-line arguments.
Argo CD uses both gRPC and HTTPS protocols on the same port (443). This creates a challenge when defining a single NGINX ingress object and rule for the argocd-service. The nginx.ingress.kubernetes.io/backend-protocol annotation only accepts a single value for the backend protocol (e.g., HTTP, HTTPS, GRPC, GRPCS).
To expose the Argo CD API server with a single ingress rule and hostname, we use the nginx.ingress.kubernetes.io/ssl-passthrough annotation. This annotation enables passing through TLS connections and terminates TLS at the Argo CD API server.
The way you edit the deployment depends on your setup. In your scenario, the ingress controller is deployed via a deployment, but it can also be deployed via a DaemonSet in other setups (e.g., RKE2 clusters). Regardless of the deployment method, you need to check and update the configuration by adding – -enable-ssl-passthrough to the container arguments section.
3: Deploying Argo CD with Helm
With preparations complete, it’s time to deploy Argo CD. Start by adding the Argo CD Helm repository and updating it:
helm repo add argo https://argoproj.github.io/argo-helmhelm repo updateRun the following command to deploy Argo CD. This command installs the argo-cd application from the argo Helm repository, specifying version 6.6.0. It also sets several configuration options:
- global.domain: Sets the domain name for Argo CD (replace argocd.kanzal.com with your desired domain name).
- server.ingress.enabled: Enables the NGINX ingress controller for Argo CD.
- server.ingress.ingressClassName: Sets the ingress class name to nginx.
- server.ingress.annotations: Sets annotations for the NGINX ingress controller:
- nginx.ingress.kubernetes.io/force-ssl-redirect: Forces HTTPS redirection.
- nginx.ingress.kubernetes.io/ssl-passthrough: Enables SSL passthrough to Argo CD.
- server.ingress.tls: Enables TLS for Argo CD.
helm upgrade --install argocd argo/argo-cd --version 6.6.0 \
--set global.domain=<your-domain.com> \
--set server.ingress.enabled=true \
--set server.ingress.ingressClassName=nginx \
--set server.ingress.annotations."nginx\.ingress\.kubernetes\.io/force-ssl-redirect"="true" \
--set server.ingress.annotations."nginx\.ingress\.kubernetes\.io/ssl-passthrough"="true" \
--set server.ingress.tls=true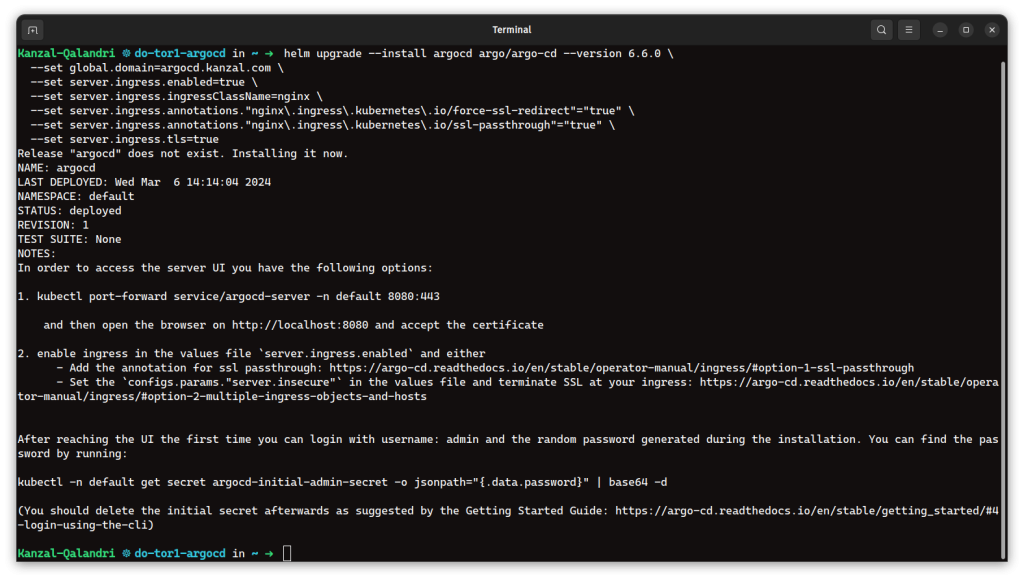
This command deploys Argo CD, making it accessible at <your-domain.com> with a secure connection.
You can verify the installation by running the following command:
helm list4: Updating DNS Records
Argo CD is now installed, but you won’t be able to access it directly through your browser yet. To enable access, follow these steps:
a) Obtain the Load Balancer IP
Run the following command to retrieve the Load Balancer IP address:
kubectl get ingress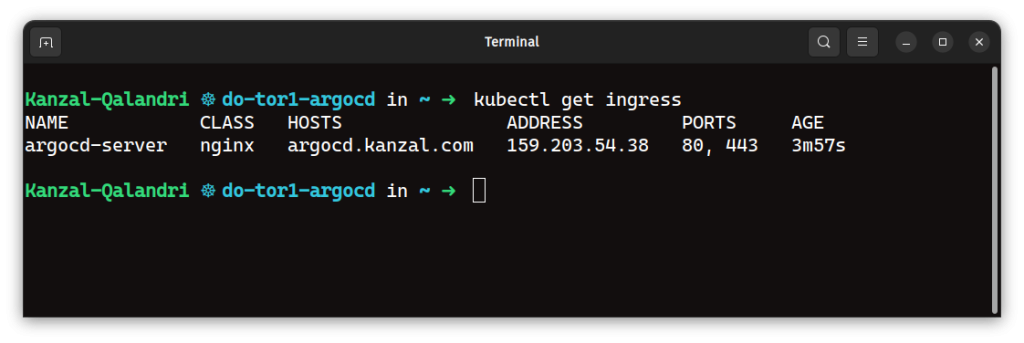
Look for an ingress resource named “argocd-server” and copy its address.
b) Update your Domain’s DNS Record
Log in to your DNS management console (e.g., Cloudflare) and add a new DNS record for your chosen domain name.
- Record Type: A record
- Name: Use your desired subdomain (e.g., “<your-subdomain>[invalid URL removed]”)
- Value: Paste the copied Load Balancer IP address
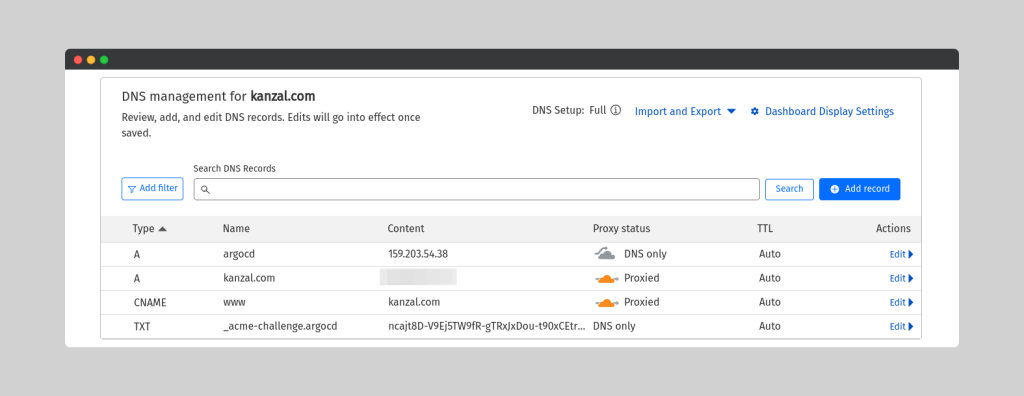
Note: The specific steps for adding a DNS record may vary depending on your DNS provider. Refer to their documentation for detailed instructions.
Once you’ve added the DNS record, it may take some time for the changes to propagate throughout the internet. After propagation, you should be able to access Argo CD by visiting your chosen subdomain in a web browser.
5: Verifying the Installation
Now it’s time to verify the deployment. Head to your chosen domain name in your web browser. In my example, I’ll be checking argocd.kanzal.com.
You should see Argo CD running and secured with HTTPS.
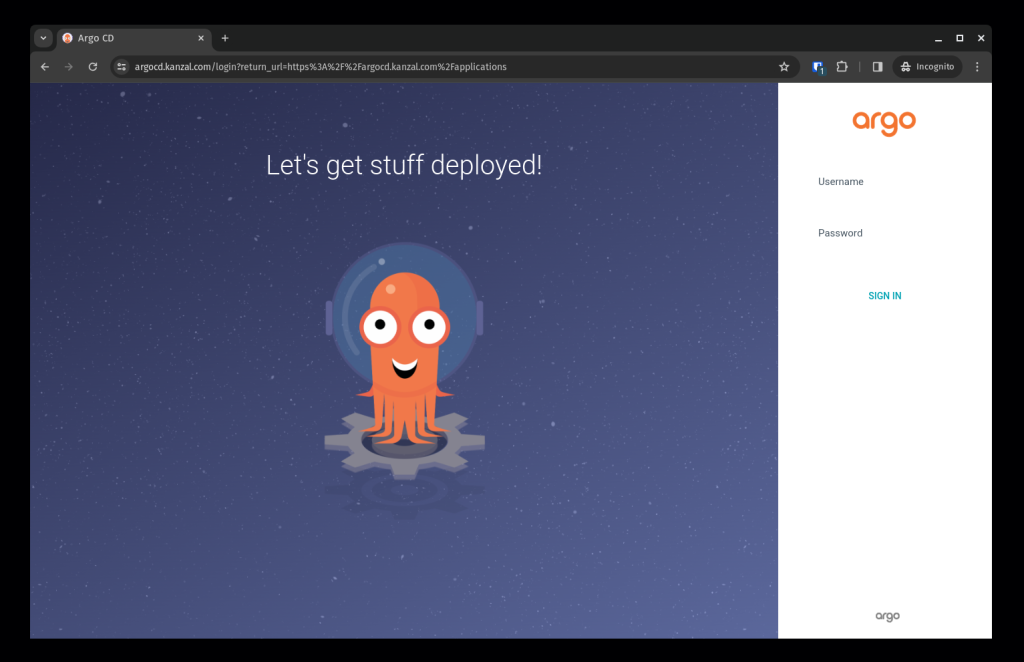
To log in to Argo CD, you’ll need the initial admin password. Here’s how to obtain it:
Run the following command to retrieve the password:
kubectl get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echoNote: This command retrieves the initial admin password stored as a secret in Kubernetes. It’s recommended to change the password after your initial login for security reasons.
Username: Use the default username admin.
Password: Paste the copied password from the previous step.
Conclusion
Argo CD is now deployed!
Important Note: This setup isn’t ideal for production environments. In production, you’ll need:
- Trusted SSL certificates: Get them from a trusted provider or use cert-manager for automatic renewal.
- High availability (HA): Set up HA mode with autoscaling for better reliability.
If you encounter any issues, feel free to ask in the comments below!